Microsoft Defender - Overview of the security offering
In this blog post you get a quick overview of the extensive microsoft defender product suite / security offering.

Microsoft Defender Suite
Microsoft recently rebranded its Microsoft Advanced Threat Protection (ATP) offering and now markets its products under the Microsoft Defender name. We would like to take this opportunity to provide an overview of the existing products.
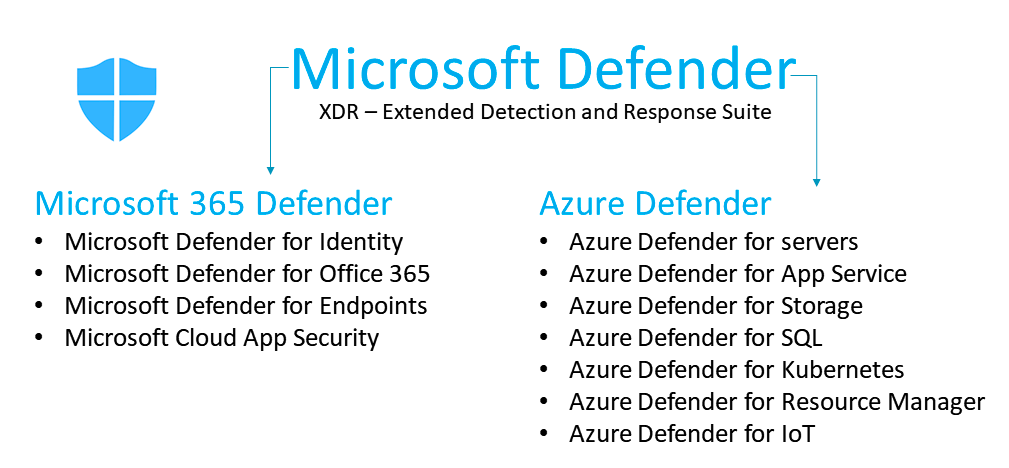
Microsoft Defender is a comprehensive solution, also known as eXtended Detection and Response (XDR). It provides protection on end-user environments/devices, cloud services and on-premises applications to effectively stop potential attackers. There are now two main classifications: Microsoft 365 Defender and Azure Defender. Product names starting with “Azure Defender for” are used to protect Azure resources. The corresponding license is included in the "Azure Security Center" offer. Product names beginning with "Microsoft Defender for" are used to protect Microsoft cloud services such as Microsoft 365 and the corresponding licenses are included in the "Microsoft 365 E5" offer or can also be licensed individually.
Microsoft 365 Defender
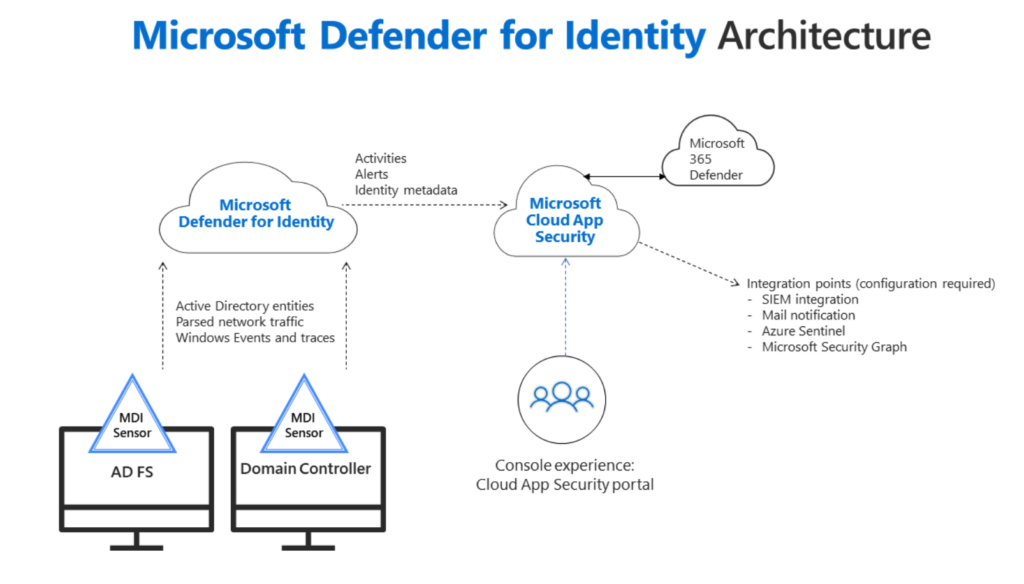
Microsoft Defender for Identity
This product is used to monitor your local Active Directory, as well as any ADFS server. To do this, you install smaller software (Defender for Identity software), which collects the relevant data locally and sends it to the Microsoft cloud. On your online portal (Defender for Identity Portal) you can then examine the data for threats, compromised identities / accounts and suspicious activities.
Microsoft Defender for Office 365
With this Defender module you monitor the popular Office 365 services and protect yourself effectively against threats such as phishing emails, unsafe links and also includes protection for attachments on Sharepoint, Onedrive and Microsoft Teams. Further information
| Defender for Office 365 Plan 1 | Defender for Office 365 Plan 2 |
| Configuration, protection, and detection capabilities: Safe Attachments Safe Links Safe Attachments for SharePoint, OneDrive, and Microsoft Teams Anti-phishing protection in Defender for Office 365 Real-time detections | Defender for Office 365 Plan 1 capabilities— plus — Automation, investigation, remediation, and education capabilities: Threat Trackers Threat Explorer Automated investigation and response Attack Simulator |
Microsoft Defender for Endpoint
This is Microsoft's endpoint security solution. Not only can you protect Windows 10 based devices, but also iOS, iPad OS, macOS and Android devices. Microsoft Defender for Endpoint uses artificial intelligence (machine learning) to better detect attacks and can react automatically.
Microsoft Cloud App Security (CASB)
Users often work with a wide range of cloud services / cloud applications (e.g. Dropbox, Amazon Web Services, Office 365) - sometimes without the knowledge of IT. The Microsoft Cloud App Security helps to detect the use of so-called "Shadow IT" applications. The associated risk can then be evaluated and a decision made on how to proceed with the cloud app.
Azure Defender
The Azure Defender protects all Azure resources such as VMs, apps, services or Azure SQL from attacks.
Azure Defender for Servers
This is the virus scanner that can be used to protect virtual machines (regardless of whether they are on Azure or with a third party provider). Windows-based and Linux-based servers are supported.
The service offers the following useful features, among others:
Vulnerability Assessment
The VM's / servers are scanned for vulnerabilities using the Qualys Cloud Service. The results of the scanning are sent back to the Azure Security Center. The results include a list of vulnerabilities found in the installed software products running on the VM.
Just in Time Access
Various ports are opened in the firewall only when an authorized user wants to use the appropriate services.
Adaptive Application Controls
This feature compiles an intelligent and automated whitelist of known programs that are allowed to run on the VM's. Machine learning is used for the analysis to identify programs that are frequently used in your organization. If a program that is not on the whitelist is running, an alarm can be triggered.
Azure Defender for App Service
The Azure Defender for App Service runs as a layer in the security stack of Microsoft's PaaS offering and helps to detect and prevent attacks on your web services (Azure App Service). The service is used to detect suspicious traffic and outdated DNS entries. Further information can be found on the Microsoft homepage.
Azure Defender for Storage
More and more companies are storing their data with PaaS storage providers such as Azure Storage. With the increasing use of this offer, the risk of cyber attacks and data leaks in relation to business-critical data also increases.
Azure Defender for SQL
With the Azure Defender for SQL you can protect your cloud-based SQL Server (Azure) as well as on-premise installations. A vulnerability assessment service warns you of potential vulnerabilities and helps you fix them. Microsoft promises that when developing this Defender Service, priority was given to performance, so that this is only slightly affected by the scanning.
Azure Defender for Kubernetes
Of course, Microsoft has also created a Managed Kubernetes offering (AKS) in its Azure Cloud.
Azure Defender for Kubernetes provides cluster-level threat protection by monitoring your clusters’ logs.Quelle: Microsoft Homepage
The security of the Kubernetes cluster is monitored using the logs. The Azure Defender for Kubernetes searches for security-related events such as the creation of new privileged accounts or freely accessible Kubernetes dashboards. Here is a list of events that are monitored. We will look at Azure Defender for Kubernetes in more detail in a future blog post.
Azure Defender for Resource Manager
The Azure Defender for Resource Manager monitors the resources in Azure (create, update, delete) and manages features such as access permissions, locks, tags to ensure the security of all resources after their creation. An alert can be set up for suspicious activity.
Azure Defender for IoT
This is a specialized environment for IoT solutions. For IoT device developers, Azure Defender for IoT provides lightweight agents to ensure device-level security for new IoT/OT projects.
