Microsoft Defender for Office 365 - Best Practice Deep Dive
E-Mail Security: Mail Flow Deep Dive und Microsoft Defender for Office 365 Best Practice Configuration.

The Microsoft Defender for Office 365 is a very central part of the Microsoft Security Suite and there are many adjustment screws. How do you keep track of that?
Today’s blog post is about the Microsoft Defender for Office 365 Best Practice – i.e. the configuration of “Microsoft Defender for Office 365” and “Exchange Online Protection (EOP)”.
The “Microsoft Defender for Office 365” combines useful functions.
- Exchange Online Protection (EOP)
EOP is the cloud-based filtering service that protects your organization from spam, malware, and other email threats and can now be called the core of “Microsoft Defender for Office 365” because EOP is included in all Microsoft 365 organizations with Exchange Online mailboxes . - Microsoft Defender for Office 365
The Defender for Office 365 offers advanced features for email security and is available in 2 plans. Plan 1 is included as standard in the popular “Microsoft 365 Business Premium” subscription. All the features we describe in today’s blog are included in plan 1.
Before an e-mail arrives in your inbox, it is put through its paces by EOP. In the graphic you can now see a comprehensive overview of which stages an e-mail has to go through in order to arrive in your inbox. Below we take a closer look at each station.
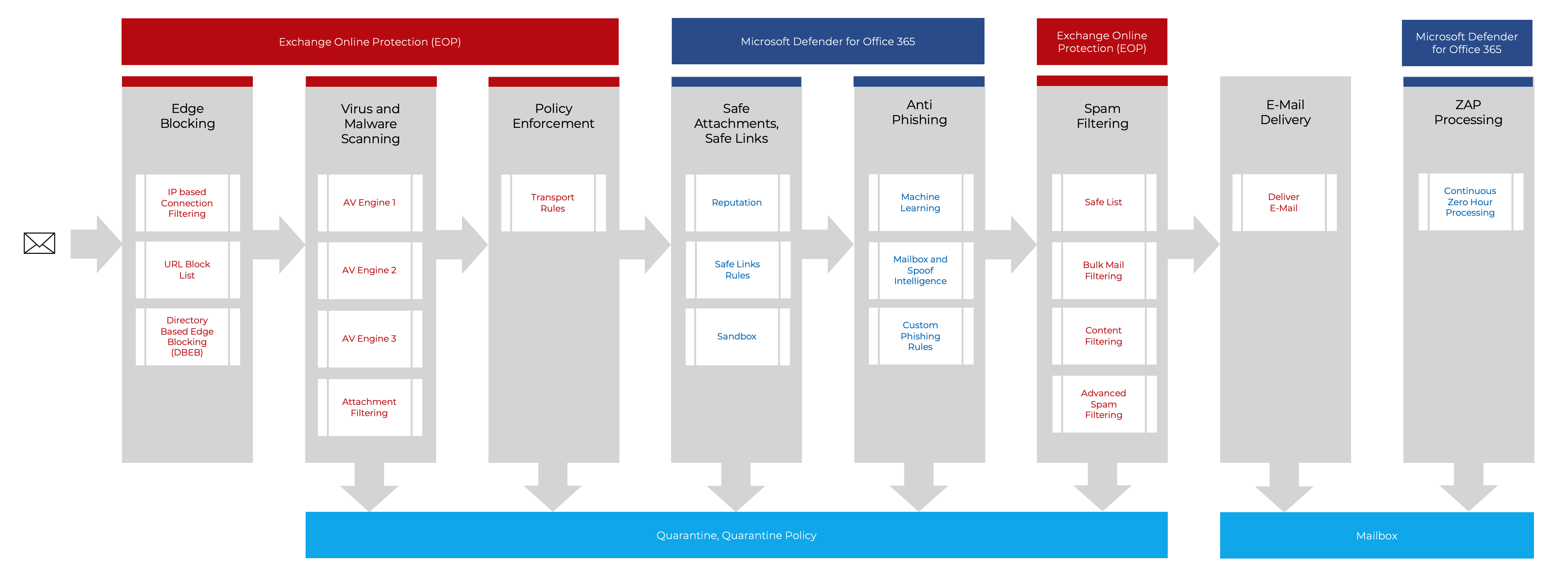
Content – Microsoft Defender for Office 365 Best Practice
We look at the following topics:
- Best Practice Configuration (ORCA)
With the tool from Microsoft, you can check all relevant settings that affect e-mail security in no time at all. - Edge Blocking (EOP)
Connection Filtering. Who sent the email. IP whitelist, IP blacklist - Virus und Malware Scanning (EOP)
Multiple engines detect virus signatures and malware - Policy Enforcement (EOP)
Mails are further routed based on the defined transport routes - Safe Attachments, Safe Links (Microsoft Defender for Office 365)
Scans Attachments and Links in you Microsoft 365 Services - Anti Phishing (Microsoft Defender for Office 365)
Machine Learning, Spoof Intelligence (DPF, DKIM, DMARC) - Spam Filter (EOP)
Rules are used to calculate a Spam Confidence Level (SCL) and a Bulk Complaint Level (BCL) for email messages. - ZAP Processing (Microsoft Defender for Office 365)
Continuous checking of the mailbox for spam and malware.
Microsoft Defender for Office 365 Best Practice Configuration
Before we take a look at the different components, we would like to draw your attention to Microsoft’s website where the best practices can be found:
Recommended settings for EOP and Microsoft Defender for Office 365 security
With the following Powershell command you can install and run the ORCA (“Office 365 Advanced Threat Protection Recommended Configuration Analyzer”) tool from the Powershell Gallery. It is an auditing tool / best practice analyzer from Microsoft. This makes the Microsoft Defender for Office 365 Best Practice configuration very easy to do.
Install-Module -Name ORCA
Get-OrcaReportThe tool generates an HTML file and shows you which security adjustment screws you should turn. Here is an example of the output from a newly created Office 365 tenant. We now look at the proposed changes to achieve a better score.
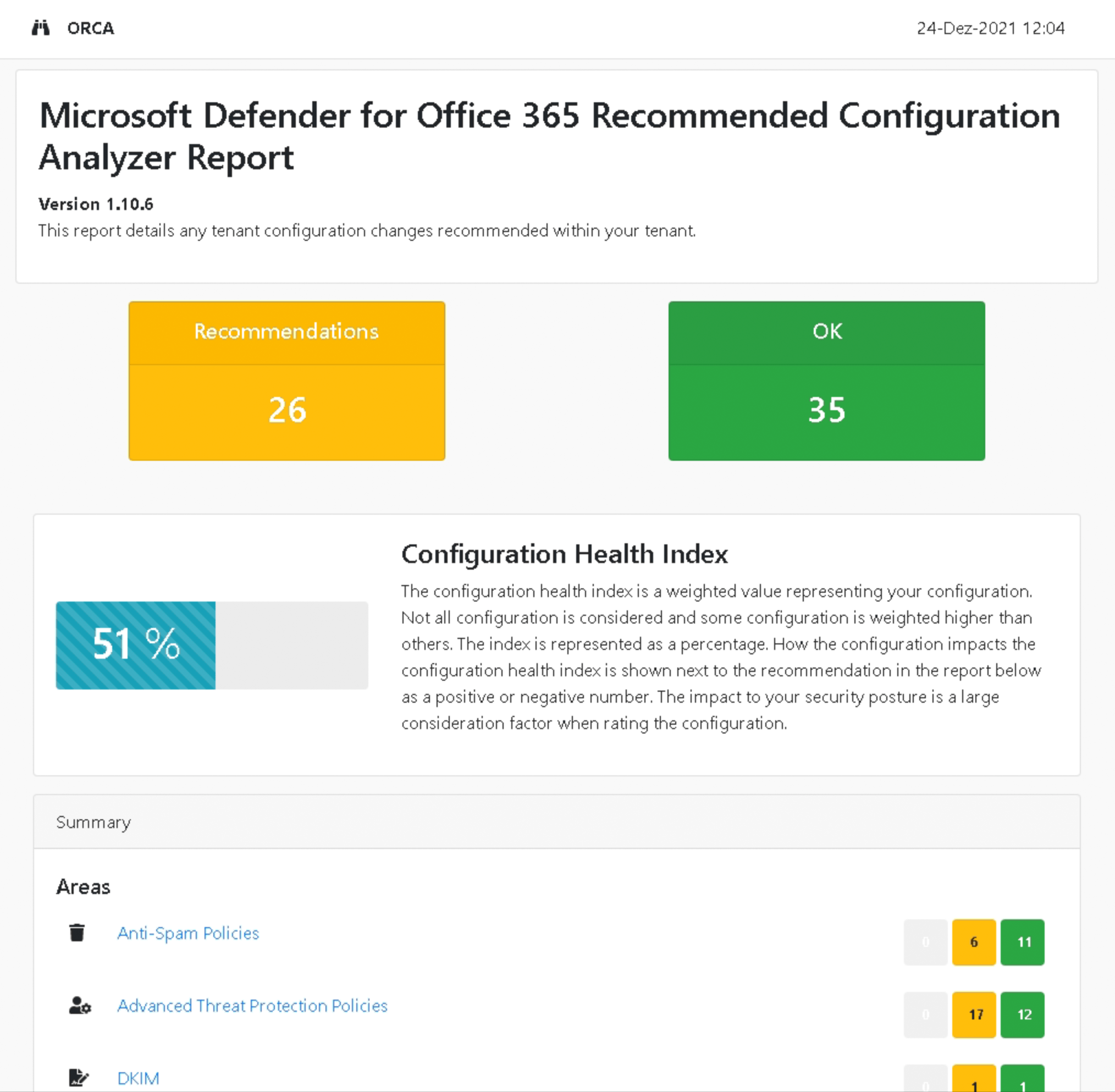
We worked through all the points in the report and ended up with a score of almost 100.
Edge Blocking
With the connection policy (connection filter) you can easily define an IP whitelist or blacklist of senders. You can do this either directly in the web portal (security.microsoft.com) or via Powershell. The commands can be found in the instructions on this page.
Virus and Malware Scanning
EOP uses at least three anti-malware engines to provide optimal protection against both known and unknown email threats. The antimalware engines scan the body text of the e-mail, as well as all attachments. If an e-mail contains signatures (parts of code) from known viruses, it will be blocked. In the background, EOP checks for new virus signatures every 15 minutes and updates its engine. If a virus breaks out globally, the engines are also updated manually by the specialists so that all Microsoft customers can benefit.
Exactly how the engines work is of course Microsoft’s company secret and not publicly documented.
Links
Policy Enforcement
EOP mail flow policies come into play early in the mail flow. For example, you have the option of bypassing spam filtering. Or stop an outgoing email if confidential information (e.g. account numbers) was detected in the content. You can set the mail flow rules in the Exchange Online Admin Center.
Links
- Microsoft – Mail flow rules (transport rules) in Exchange Online
- Configuration – Mail Flow Rules in Exchange Admin Center
Safe Attachments, Safe Links
If you configure the Safe Attachments Policy, attachments in emails that have also previously been scanned with Anti Malware Protection (EOP) are replaced with a link. When you click/open the attachment, it is previously sandboxed or “detonated” in the background to see if it’s safe.
If you turn on the Safe Links Policy, URLs in emails will be rewritten to e.g. “https://eur03.safelinks.protection.outlook.com/?url=” (the user sees the original URL visually). This allows Microsoft to scan the landing page with your scanning service when clicked.
You can test whether the policy is working correctly by sending yourself an e-mail containing the following link: http://www.spamlink.contoso.com
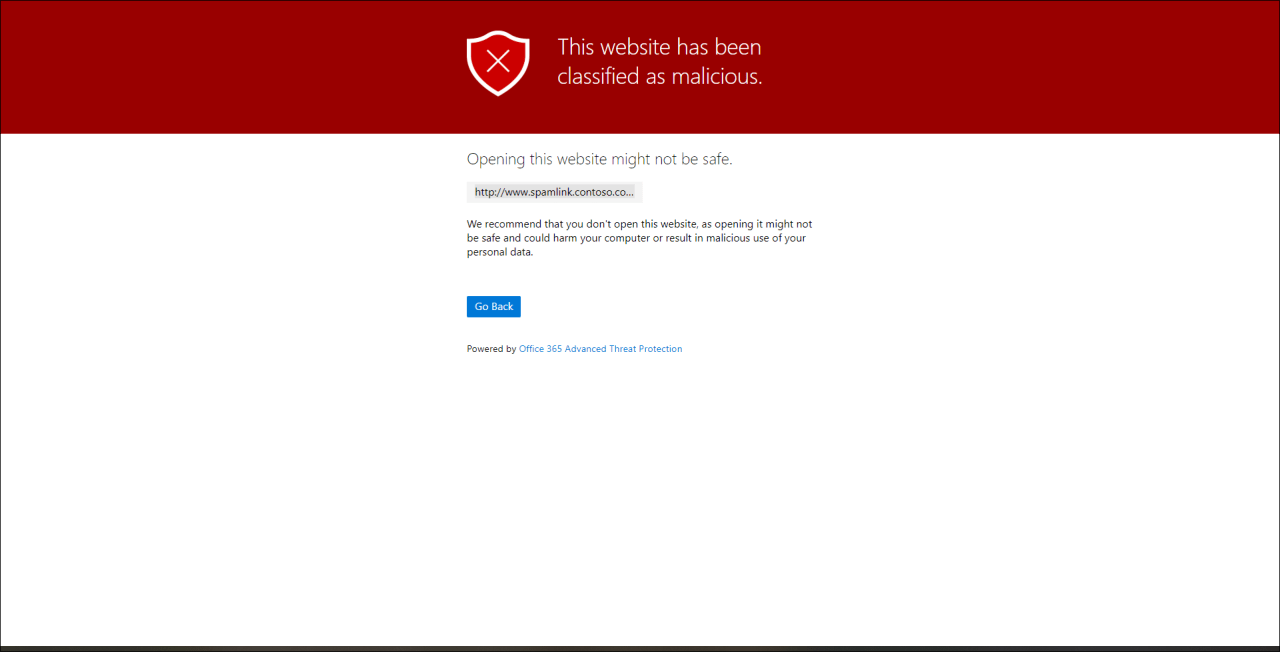
Links
- Microsoft – Safe Links in Microsoft Defender for Office 365
- Microsoft – Safe Attachments in Microsoft Defender for Office 365
- Configuration – Safe Links in Security Center
Anti Phishing
Anti-Phishing uses artificial intelligence (mailbox intelligence) to determine who is impersonating you based on the messages in your mailbox. An example from the Microsoft documentation:
For example, Gabriela Laureano (glaureano@contoso.com) is the CEO of your company, so you add her as a protected sender in the Enable users to protect settings of the policy. But, some of the recipients that the policy applies to communicate regularly with a vendor who is also named Gabriela Laureano (glaureano@fabrikam.com). Because those recipients have a communication history with glaureano@fabrikam.com, mailbox intelligence will not identify messages from glaureano@fabrikam.com as an impersonation attempt of glaureano@contoso.com for those recipients.Example – Anti Phishing Mailbox Intelligence
Of course, anti-phishing also includes anti-spoofing (“spoof intelligence: on”). In spoofed emails, a hacker pretends to be someone else to trick you into revealing sensitive information. Anti-spoofing is based on checking the sender’s SPF, DKIM and DMARC records. A topic for a separate blog post. By the way, you can see exactly how to set these records correctly in your own environment when you run the ORCA tool that was already mentioned.
Links
Spam Filter
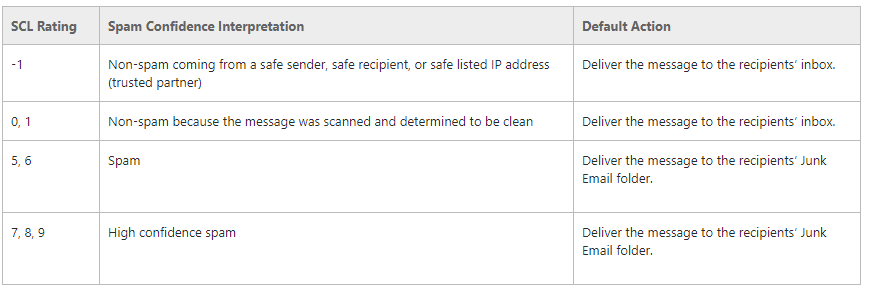
The e-mails are examined using various properties and rules and are given an SCL rating (Spam Confidence Level). For example, the SCL rating can be increased if an email contains certain “spam trigger words” such as “Order today”, “Free money”, etc.
Which rules Microsoft uses exactly is of course not publicly documented. However, if your e-mail arrives in the mailbox, you can see the calculated spam confidence level in the e-mail header (e.g.: “X-MS-Exchange-Organization-SCL: 1”). From a spam confidence level of 5, EOP has declared the e-mail as spam.
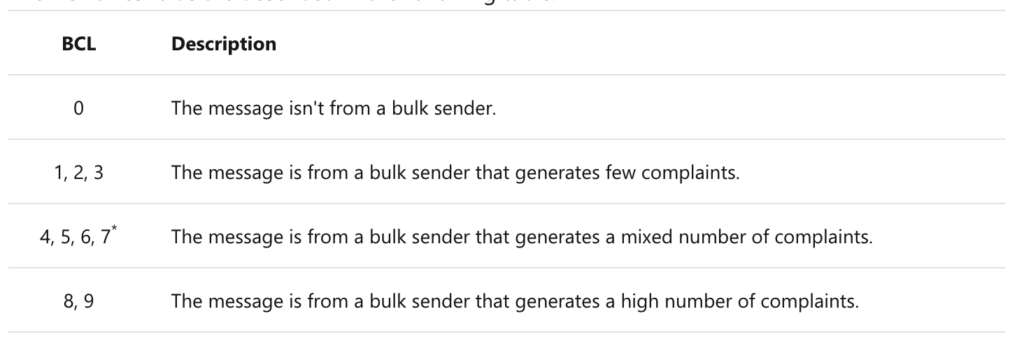
You can set the Bulk Complaint Level (BCL) yourself in the Antispam Policy. The more “bulk complaints” a sender has, the more likely it is that it is a bulk sender / spam sender. Therefore, if you increase the “Bulky email threshold” value in the anti-spam policy, you increase the tolerance for the BCL. Microsoft recommends defining a value of 6.
Links
ZAP Processing
The Zero Hour Auto Purge scans emails that have already been delivered to your mailbox. It may be that it contains e-mails that were not previously recognized as spam or malware, but are classified as malware according to more recent detection guidelines. ZAP Is on by default – you should set your spam action in the security center to “Move message to Junk Email Folder” (default setting).
Links
Powershell
Finally, some useful Powershell commands to easily view / check the Microsoft Defender for Office 365 policies.
# Verbindungsfilterrichtlinie / Connection Filter
Get-HostedConnectionFilterPolicy
# Antispam Richtlinie
Get-HostedContentFilterPolicy
Get-HostedContentFilterRule
Get-HostedOutboundSpamFilterPolicy
# Anti Phishing
Get-AntiphishPolicy
Get-AntiPhishRule
# Anti Malware
Get-MalwareFilterPolicy
Get-MalwareFilterRule
# Transport Rules
Get-TransportRule
# Safe Links / Safe Attachments
Get-AtpPolicyForO365
Get-SafeAttachmentPolicy
Get-SafeAttachmentRule
Get-SafeLinksPolicy
Get-SafeLinksRule
# DKIM Configuration
Get-DkimSigningConfigConclusion – Microsoft Defender for Office 365 Best Practice
As you have seen, there are many settings related to EOP and Microsoft Defender Microsoft for Office 365. The ORCA Utility is a very good help in configuring Microsoft Defender for Office 365 according to best practice.
Did you find this article helpful? Please help us to improve:
